Ransomware attacks! What do field service business owners need to know?
By My Service Depot on Tuesday, November 24, 2020Ransomware can seriously disrupt your field service business. Find out how you can protect yourself.
As a field service business owner, you probably don’t spend much time thinking about ransomware. According to the numbers though, you probably should:
- One in five small and medium size businesses (SMBs) have been the victims of ransomware attacks. 1
- The average ransom is approximately $5,900.1
- Downtime costs are 23 times more than the ransom.1
So, what is ransomware?
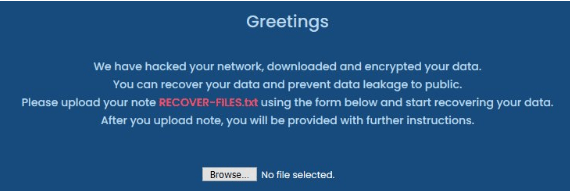
Ransomware will encrypt your database files, QuickBooks company files, and other critical business files. Then, it will display instructions on how to pay the ransom before the ransomers decrypt the files (essentially holding your critical data hostage). If you pay the ransom, there is a good chance the ransomers will ask for additional payments and you will still not get the decryption key.2 This will shut down your office computer operations and your field service technicians will not be able to send or receive important job updates.
Where does ransomware come from?
The most likely ways your business will fall victim to a ransomware attack? Malicious emails and malicious websites.3
Malicious emails may contain malicious links or attachments. The emails may look exactly like a legitimate email from your bank, credit card company, someone you know, an executive in your company, or even major websites and services like Amazon or PayPal. The moment you click on the malicious link or attachment, the ransomware is downloaded, your system is infected, and your files are held for ransom.
Malicious or compromised websites can be even more difficult to avoid. Some may attempt to frighten you with a browser popup that you have been infected. They may claim to be from well-known companies like Microsoft and instruct you to call them immediately, at which time they will ask you to go to a legitimate help assistance website and instruct you to give them remote control of your computer. Other browser popups pose even greater dangers; simply clicking to close the popup can infect your computer. Worse yet, some malicious websites may infect your computer as soon as you visit the website; you don’t have to click on anything.4 Once the page loads, it’s too late!
Preventing Ransomware
The adage “an ounce of prevention is worth a pound of cure” goes a long way with ransomware.
Do not click on any email links or open any email attachments if you were not expecting them. For example, if you forgot your password for a website and you used their link to reset your password, then you received an email from them a minute later with the reset link; that is an email you initiated and are expecting; use it. If you receive what looks like an email from your bank with a link to open your account and fix an issue, avoid that link like the plague. If you think it might be legitimate, open your bank website directly from your browser and log in that way to see if there really is an issue. Another safe alternative is to call your bank directly and ask about the email. Don’t use the phone number from a questionable email; look the phone number up from the official website contact page instead.
Keep Windows updates current on all machines. “Drive-by downloads” that come from malicious websites will typically exploit older system weaknesses. More recent software updates have safeguards against these tactics.
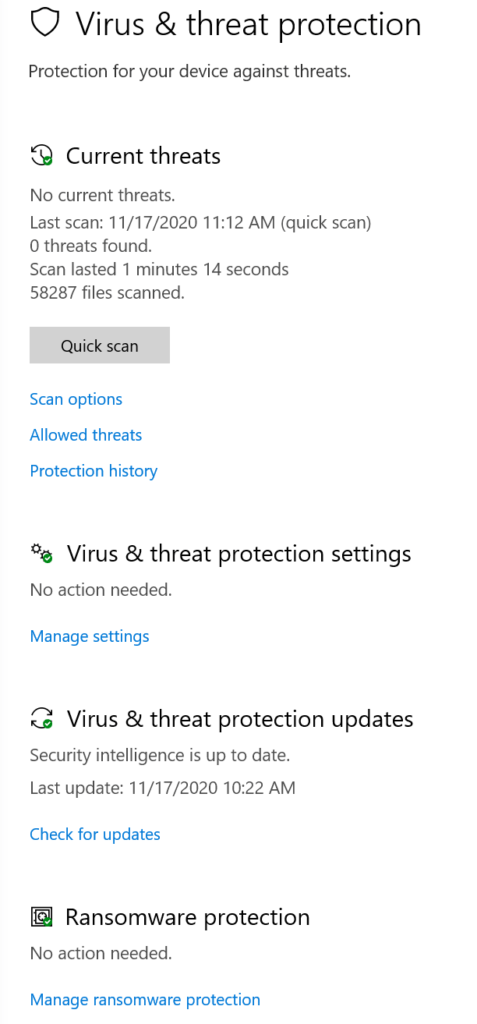
Use a current operating system on all machines. Windows 10 and Windows Server 2019 are more secure than their older predecessors5 and come equipped with the latest Microsoft Windows Security. Windows Security is on par with McAfee and Norton, so you can stop paying for those specialized programs.6 With Windows 10 and Windows Server 2019, open Windows Security from Settings, Update & Security, and follow all of its recommendations. This wonderful security suite offers real-time protection for email and web browsing. Take the time to review all of its features and recommendations. Recommended features include isolated browsing, exploit protection, and more specifically, ransomware protection with controlled folder access.
Use Microsoft Edge browser with Microsoft Defender Application Guard installed. The latest Edge is fast and based on the Chromium browser engine. Microsoft Defender Application Guard launches Edge in an isolated container that is separate from the host operating system.7,8 If your office staff uses Google Docs a lot, you’ll still want to use Chrome for that; just make sure to keep it current with the recommended security features enabled.

Protect your critical database and company files with regular, offsite backups. If you haven’t done so already, read our series Regularly Backing Up Your SQL Server Database. Regular, frequent backups form the baseline of good business continuity and disaster recovery. Now, take the additional step of regular, offsite backups. Maintain two external drives dedicated for this purpose. Once per week at a minimum, attach one of the external drives to your server and copy your current database backup file to it. Run QuickBooks company file backup to the external drive. Also, copy any other important business documents to the external drive. At the end of the day, take the external drive home with you so your data is protected from disasters like floods, fires, robberies, and ransomware attacks. Alternate between the two external drives for additional redundancy in case one disk becomes corrupted or damaged. Solid state drives (SSD) are recommended for better operational performance and physical ruggedness compared to older, spinning disk drives (HDD). These may seem like extreme steps, but with the future of your business (and the livelihood of all your employees) on the line, you can’t afford to take chances.
Educate yourself and train your staff about security concerns and practices. One great place to start is Protecting Against Ransomware | CISA. Download, complete, and post this helpful poster template from CISA in the workplace: PSAP_Ransomware_Poster_template_v3 6.11.20 (508 Version).pdf. Train your field service technicians about mobile device security threats and precautions to take.
Summing It All Up
- Be aware of the threat posed by ransomware attacks.
- Do not click on any email links or open any email attachments if you were not expecting them.
- Use a current operating system on all machines and keep Windows updates current.
- Implement Windows Security and follow its recommendations.
- Use Microsoft Edge browser with Microsoft Defender Application Guard installed.
- Protect your critical database and company files with regular, offsite backups.
- Educate yourself and train your staff about security concerns and practices.
Don’t wait until it’s too late. Be aware of the constant risks to your business’ technology and data and how much it will cost if you become a victim. Take the steps necessary to prevent a ransomware attack from happening to you.
References:
1https://www.datto.com/resource-downloads/Datto2019_StateOfTheChannel_RansomwareReport.pdf
2https://us-cert.cisa.gov/ncas/tips/ST19-001
3https://www.paloaltonetworks.com/cyberpedia/ransomware-common-attack-methods
4https://www.kaspersky.com/resource-center/definitions/drive-by-download
5https://www.howtogeek.com/401648/dont-downgrade-from-windows-10-to-windows-8.1/
6https://www.pcworld.com/article/3434097/why-you-can-stop-paying-for-antivirus-software.html